Dr. Lin Develops Computer Security Techniques
Dr. Lin has developed low-level security techniques to defend computers against viruses and other threats! Computer viruses are tricky, but Dr. Zhiqiang Lin has developed computer software to out smart them! To understand why his approach is so effective, a diagram and some background information in computer basics is needed.
Pictured above is Dr. Zhiqiang Lin (center) with some of his current graduate students at the University of Texas at Dallas (UTDallas). The diagrams, below, show where Dr. Lin’s anti-virus software is located on a computer.
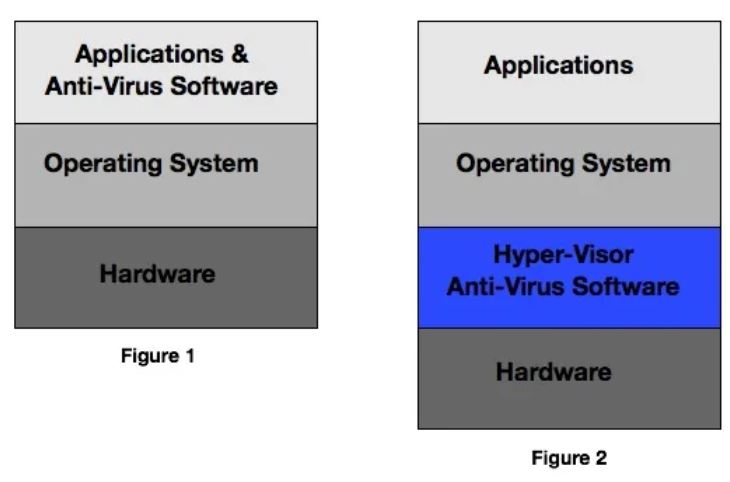
The first diagram shows how computer applications are layered above the operating system and hardware on a typical computer. It also shows where anti-virus software, like MacAfee or Norton, is usually located. The second diagram shows where Dr. Lin’s hypervisor anti-virus software is located.
“Location, Location, Location” is often the advice given to homebuyers. It is also the reason the hypervisor anti-virus software is so effective. By locating the hypervisor below the operating system, it is virtually impossible for computer viruses and other threats to work around it or disable it.
There are no standard abstractions for developing the anti-virus software at hypervisor layer. The data it observes are all 1’s and 0’s, without any meaningful information. Therefore, anti-virus software running at hypervisor layer must reconstruct the meanings from these raw data. With his students, Dr. Lin has developed techniques to make it much easier for hypervisor programmers to write the security software that runs below the operating system.
A significant advantage of running security software from a low-level vantage point is that the hypervisor can monitor computer activity and easily identify abnormal or suspicious activity from viruses and other threats. On a system of networked computers, the hypervisor on one computer can monitor another computer for any suspicious activity and if a virus is found, it can also shut down the remote computer if necessary.
Some users may be familiar with the VMware Fusion computer software utility. Among other things, it can be used on a MAC computer to support a Windows environment. The Windows operating system runs on top of the VMware Fusion utility. The VMware Corporation has been supporting Dr. Lin’s research with a research gift since 2012.
In addition to hypervisor related research, Dr. Lin also works on binary code analysis and digital forensics. Much like fingerprints and partial-prints are tracked in criminal investigations, virus software can be compared to a bank of known virus software routines with known authors or groups. In some cases, the virus code will match a routine, stored in the data bank. In other cases, the programming style of the virus can be matched with the style of known virus code. The virus code being analyzed is in machine or binary code (all 1’s and 0’s) so it is not a simple task to find a match or similar style in the data bank.
One application of Dr. Lin’s binary code analysis is source code recovery and reuse. Before high-level code or applications can be run, the source code must be compiled and linked to create an executable or binary version of the code. If changes are needed, the source code can be updated then compiled and linked to create another executable version of the code. Updates can only be made to the source code so it is important to keep it. Sometimes, on older legacy systems, a company will run executable code for several years, before changes are needed. If the source code has been lost, the executable code can be used to reconstruct the source code with some recent techniques developed by Dr. Lin and his students.
In January 2014, the Air Force Office of Scientific Research (AFOSR) awarded approximately $15.5 million in grants to 42 scientists and engineers from 32 research institutions who submitted winning research proposals through the Air Force’s Young Investigator Research Program (YIP). This year the AFOSR received 234 proposals, including Dr. Lin’s proposal, Towards Fundamental and Binary-Centric Techniques for Kernal Malware Defense. Dr. Lin was one of the 42 recipients of the prestigious AFOSR award. The objective of this program, stated on the AFOSR website (www.wpafb.af.mil/news/story.asp?id=123377864), is to “foster creative basic research in science and engineering, enhance early career development of outstanding young investigators, and increase opportunities for the young investigators to recognize the Air Force mission and the related challenges in science and engineering.”
Dr. Zhiqiang Lin is an Assistant Professor of Computer Science at The University of Texas at Dallas [www.utdallas.edu/~zhiqiang.lin]. His current research interests are: Software Security, Systems Security, Cloud Computing, Digital Forensics, and Smartphone Security.
Dr. Lin is always looking for self-motivated students with solid system (OS, virtualization, compiler, machine code) as well as security background. Interested students who wish to pursue a PhD under his direction may contact him via email at: zhiqiang.lin@utdallas.edu. Corporations and businesses interested in participating in software security research may also contact Dr. Lin via email.
The Department of Computer Science at UT Dallas [www.cs.utdallas.edu] is one of the largest CS departments in the United with more than 750 undergraduate, 500 master, and 125 PhD students. They are committed to exceptional teaching and research in a culture that is as daring as it is supportive.




